SIP攻击很常见,特别是各大云服务器,基本上开了个公网IP绑定到实例机器就会被外国IP一遍怼。防范也容易,就是把外国IP禁掉。
实现:iptables+ipset,只允许中国IP访问本机,也就实现了封禁国外IP的效果。
优点:匹配迅速,免去iptables单链匹配。
操作步骤:
1.安装ipset 以及iptabls
#安装ipset:
RedHat:yum install ipset
Debian:apt-get install ipset
#建表
ipset create china hash:net hashsize 10000 maxelem 1000000
#批量增加中国IP到ipset的china表
#以下内容保存成脚本执行即可
#!/bin/bash
rm -f cn.zone
wget http://www.ipdeny.com/ipblocks/data/countries/cn.zone
for i in `cat cn.zone`
do
ipset add china $i
done
2.创建规则文件(vim iptabls.rule):
*filter :INPUT DROP [0:0] :FORWARD DROP [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -m set --match-set china src -p tcp -m tcp --dport 1:65535 -j ACCEPT -A INPUT -m set --match-set china src -p udp -m udp --dport 1:65535 -j ACCEPT -A INPUT -p udp -m udp --dport 16384:32768 -j ACCEPT -A INPUT -s 172.18.0.0/16 -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A OUTPUT -o lo -j ACCEPT COMMIT
3.导入规则文件:
# 导入规则文件 iptables-restore < iptabls.rule # 应用生效 iptables-apply
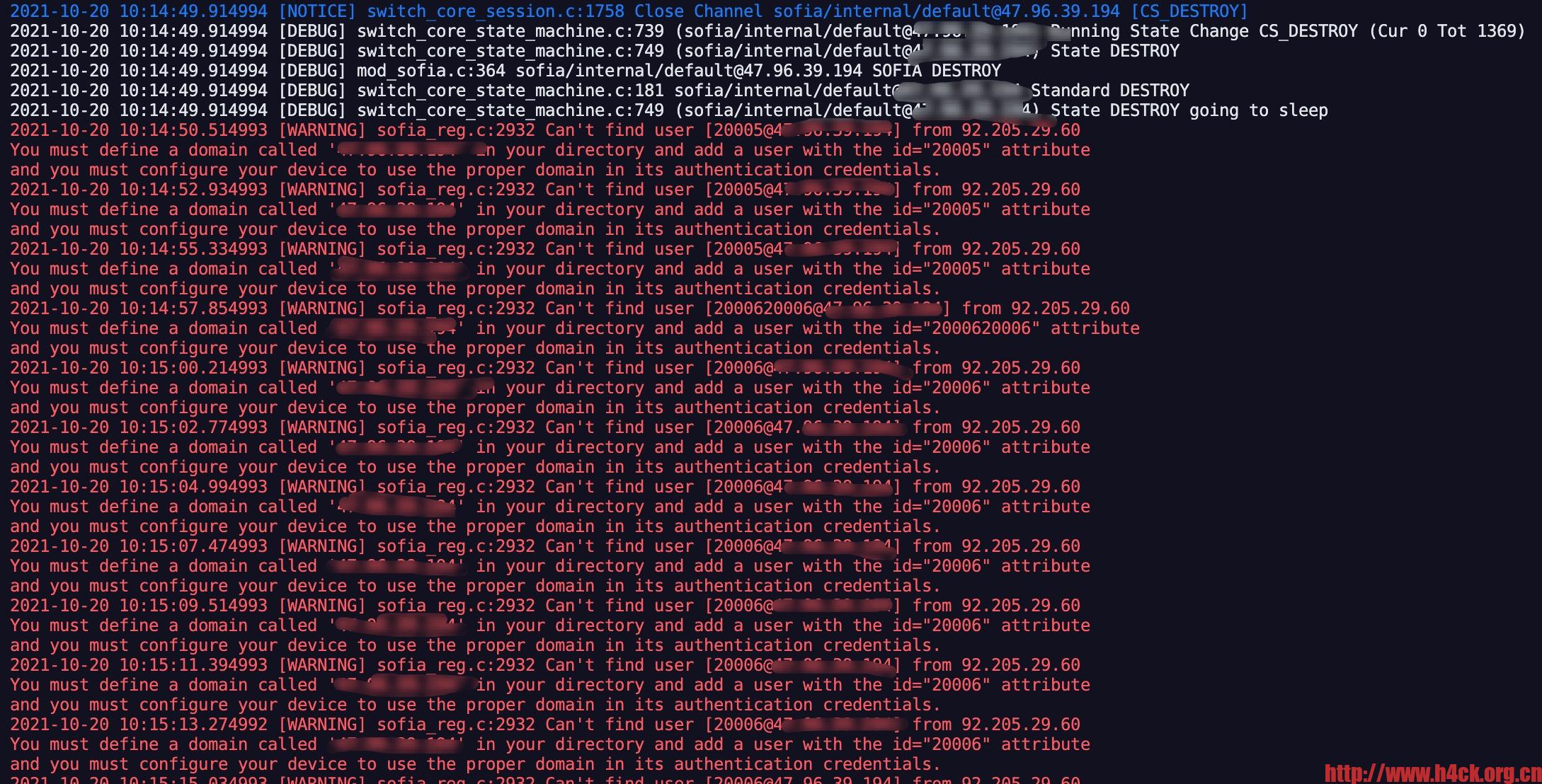
如果提示下面的错误信息:
root@opensips:~# iptables-apply Error: rulesfile not readable: /etc/network/iptables.up.rules
可以先创建iptables.up.rules文件,然后再次执行apply即可
touch /etc/network/iptables.up.rules
4.查看iptables规则:
root@opensips:~# iptables -L Chain INPUT (policy DROP) target prot opt source destination ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED ACCEPT tcp -- anywhere anywhere match-set china src tcp dpts:tcpmux:65535 ACCEPT udp -- anywhere anywhere match-set china src udp dpts:1:65535 ACCEPT udp -- anywhere anywhere udp dpts:16384:32768 ACCEPT all -- 172.18.0.0/16 anywhere ACCEPT icmp -- anywhere anywhere ACCEPT all -- anywhere anywhere Chain FORWARD (policy DROP) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere
如果看到上面的信息,iptables就生效了。现在再去看freeswitch的日志就会发现那些乱七八糟的信息都没了。
参考链接:
https://www.codeleading.com/article/6624712284/